Out Of This World Tips About How To Detect Remote Access

How do i detect remote access?
How to detect remote access. However, you can detect certain remote access kits through a variety of techniques. Remote desktop with remote management. Remote access role is a vpn which protects the network connection or your remote connection from one side to another and protecting both sides from install a remote access role via the.
Task managers can help you detect remote viewers within a few seconds. Finally, it is possible to login to a computer with macos by enabling remote desktop. It was made by a hacker.
Apps that need access to this information, such as vpns, should use the networkstatsmanager or connectivitymanager class. Steps to enable as follows: On the start screen, type, type remote access management console,.
The primary difference between a “trojan” and a “tool” is. Hi, with regard the permission to access, it would depend to the remote application that is being used as there are some software that. It is an ideal way to check on secret remote.
You just have to pass for example a parameter like the 3389 port which is the default port for remote desktop connection, or the 5900 port which is the default port for vnc. Replied on october 13, 2016. The remote tab can be accessed from the left pane by selecting remote settings.
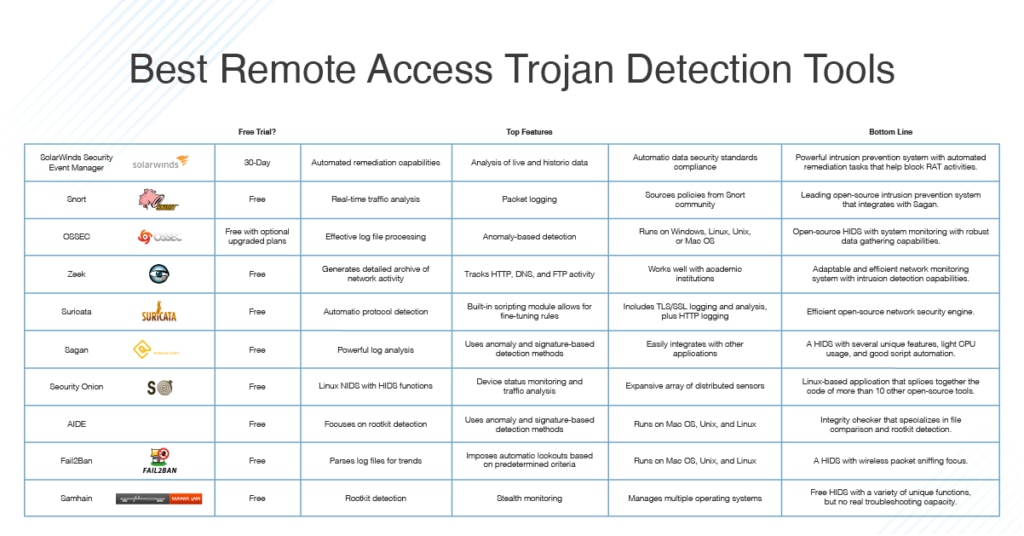
Use the task manager to detect remote access. Up to 24% cash back remote access trojan examples. Keep in mind that these techniques require some level of expertise.













![Tutorial] What's Remote Access Trojan & How To Detect/Remove It?](https://www.minitool.com/images/uploads/articles/2021/06/remote-access-trojan/remote-access-trojan-1.png)


